Regulated sectors like financial services, healthcare, life sciences, and the public sector face a difficult balance. You must move faster, reduce risk, and demonstrate continuous compliance, all while budgets and audit scrutiny rise. Choosing the right cloud solutions is not only a technical decision, it is a governance and operating model decision that affects data sovereignty, security controls, resilience, and evidence collection.
This guide distils a pragmatic approach Tasrie IT Services uses with regulated clients. It helps you evaluate cloud platforms, design guardrails, and adopt cloud native practices without compromising on compliance.
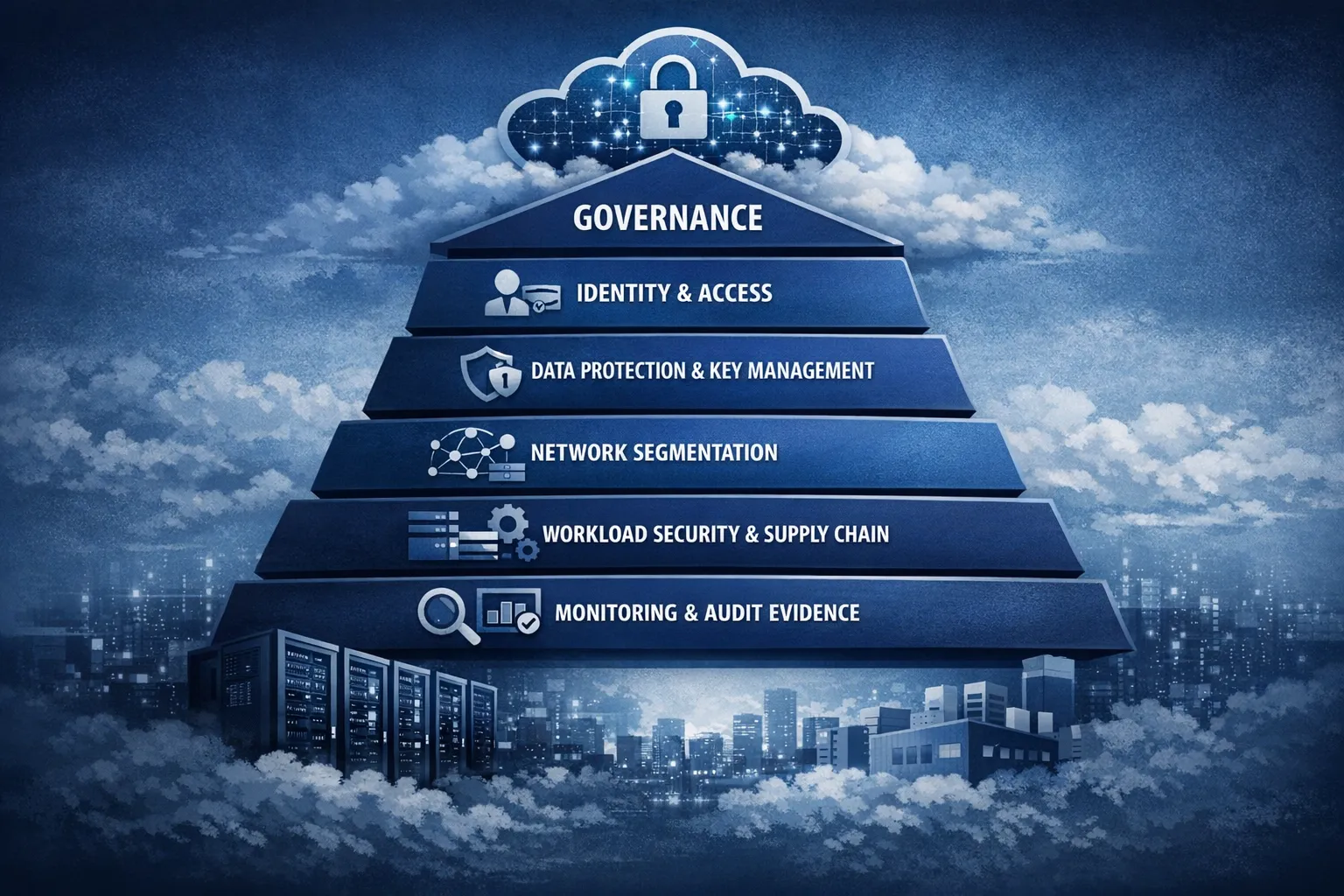
What “regulated” really means for cloud decisions
Regulation is not just a list of controls to tick off. Supervisors expect you to show how technology choices meet principles like minimising data exposure, strong identity assurance, robust resilience, and complete auditability.
- UK organisations must meet UK GDPR and the Data Protection Act 2018. The Information Commissioner’s Office provides a practical overview of obligations and accountability requirements. See the ICO’s guide to UK GDPR at ICO UK GDPR guide.
- Sector frameworks often apply in parallel. Examples include PCI DSS for payment card data, HIPAA for US health data, and GxP and 21 CFR Part 11 for electronic records in life sciences. See PCI DSS and the HIPAA Security Rule overview from HHS at HIPAA Security Rule.
- The UK National Cyber Security Centre’s Cloud Security Principles remain a solid reference for evaluating cloud providers and designs. See NCSC Cloud Security Principles.
The takeaway is simple. Map requirements to technical and procedural controls, then ensure the cloud platform, your architecture, and your DevOps practices collectively satisfy those controls with clear evidence.
A practical framework for choosing cloud solutions in regulated industries
1) Data classification and sovereignty
Start with your data. Classify by sensitivity and residency constraints. Decide where data may be processed and stored, including backups and telemetry. Most major clouds offer multiple UK and EU regions and features to limit data movement. For multi-jurisdiction organisations, design for regional isolation and explicit cross-border data flows with approvals and logging.
What good looks like: clearly documented data ownership and residency, separate environments by region, customer-managed encryption keys, immutable logging for all cross-region transfers.
2) Identity, access, and zero trust
Identity is your first control plane. Enforce single sign-on with your IdP, strong MFA, conditional access, and least privilege. Use break-glass accounts sparingly, time-bound elevated access, and continuous access reviews. Across services, prefer workload identities and short-lived credentials. Design an administrative perimeter so no privileged action requires broad internet exposure.
For architectural guidance, NIST’s zero trust model is a helpful reference. See NIST SP 800-207 Zero Trust Architecture.
3) Encryption and key management
Mandate encryption in transit and at rest for all data classes. Use customer-managed keys backed by HSMs for sensitive data, and define key rotation and separation policies. For the most stringent workloads, evaluate controls like hold-your-own-key patterns, client-side encryption, and dual control for key usage. Document and test key recovery procedures and separation of duties between security, platform, and application teams.
4) Network design and private connectivity
Default to private endpoints for platform services, restrict egress, and segment networks by environment and data classification. Adopt dedicated connectivity to on-premises where necessary, and place inspection points for egress filtering and DLP. Include DDoS protection, WAF for internet-facing applications, and explicit service-to-service allow lists rather than broad CIDR openings.
5) Observability, audit, and evidence
Regulators expect timely detection, clear incident response, and trustworthy evidence. Centralise logs and metrics, preserve them immutably, and protect time synchronisation. Stream security events into your SIEM and define runbooks for detection and response.
To deepen this capability, see our guide to Observability: Effective Monitoring which covers metrics, logs, tracing, and cloud native visibility patterns.
6) Workload and software supply chain security
Regulated workloads increasingly run on containers and Kubernetes. Enforce image provenance and signing, scan images and dependencies, and block untrusted artefacts at admission. Use network policies, secrets encryption, and baseline hardening aligned to CIS Benchmarks. For Kubernetes, Pod Security Admission and policies with Gatekeeper or Kyverno help codify guardrails.
- The Center for Internet Security provides a widely used Kubernetes hardening benchmark. See the CIS Kubernetes Benchmark.
- For supply chain integrity, the SLSA framework offers a progressive model for build provenance and tamper resistance. See slsa.dev.
Adopting GitOps strengthens auditability, because desired state and changes live in version control. Our article on why migrate to ArgoCD explains how GitOps improves compliance, rollback, and transparency for Kubernetes.
7) Resilience, backup, and disaster recovery
Define clear RTO and RPO per service. Use multi-AZ patterns for availability and consider multi-region or active-active for critical systems. Backups must be encrypted, tested, and isolated from production credentials, with retention meeting regulatory expectations. Regularly rehearse failover and restoration, then store the evidence.
Capability snapshot across the major cloud providers
The three hyperscalers provide extensive security and compliance primitives suitable for regulated workloads. Availability varies by region and service, so always confirm current status during procurement.
| Capability | AWS | Microsoft Azure | Google Cloud |
|---|---|---|---|
| Regional data residency controls | Available across multiple UK and EU regions | Available across multiple UK and EU regions | Available across multiple UK and EU regions |
| Customer managed encryption keys, HSM-backed | Available | Available | Available |
| Private service connectivity to managed services | Available | Available | Available |
| Dedicated private connectivity to on-premises | Available | Available | Available |
| Centralised audit logging and immutable retention options | Available | Available | Available |
| Managed Kubernetes with enterprise guardrails | Available | Available | Available |
| Policy as code and configuration compliance tooling | Available | Available | Available |
For a governance-level comparison of controls, many organisations map provider features to the Cloud Security Alliance’s Cloud Controls Matrix to track coverage and gaps. See the Cloud Controls Matrix.
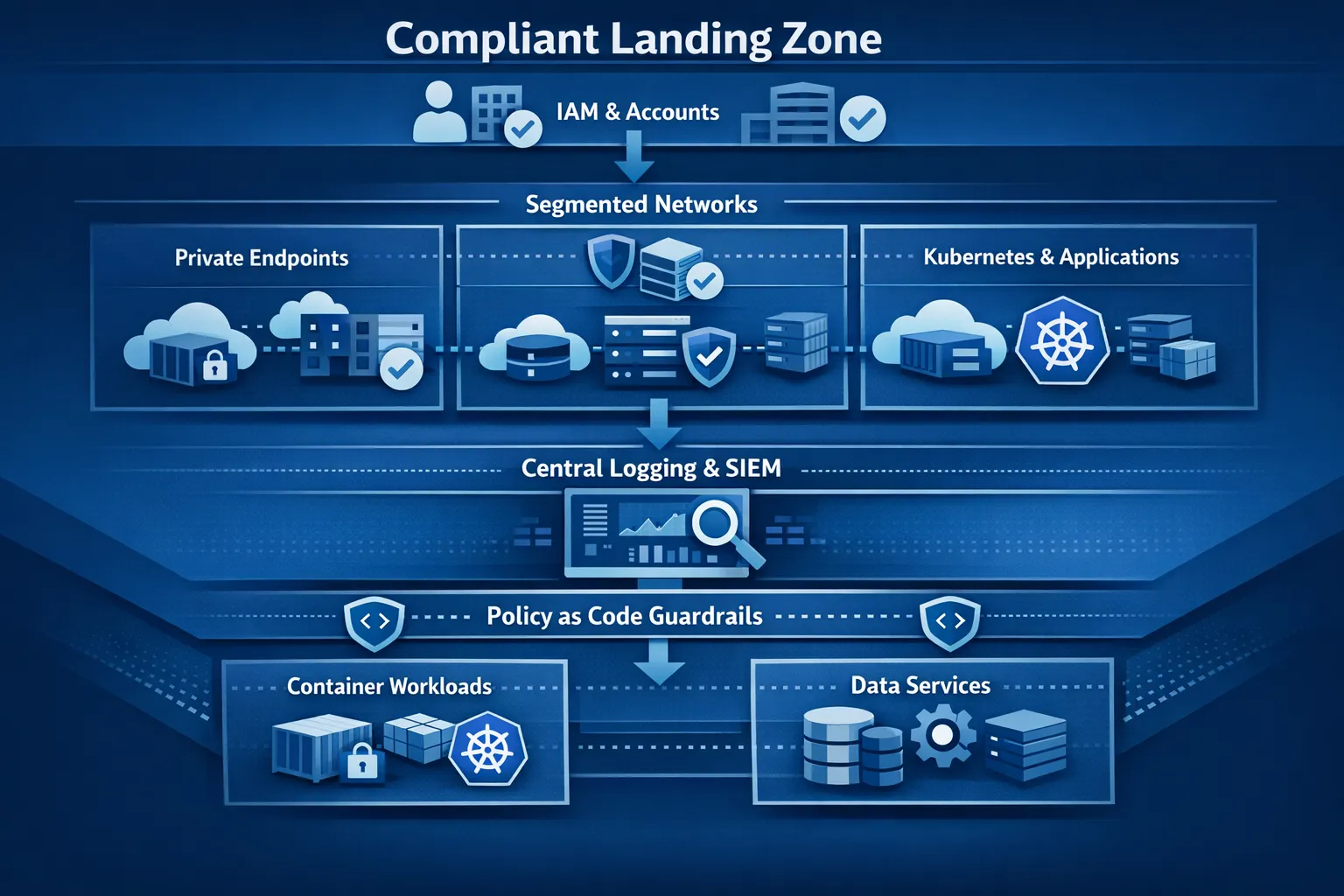
Designing a compliant landing zone
A landing zone is your opinionated, secure starting point for accounts, identity, networking, logging, and guardrails. In regulated environments the landing zone is non-negotiable because it encodes your control objectives as code.
Core elements to include:
- Identity and access baselines, including SSO integration, MFA enforcement, privileged access workflows, and account vending.
- Network foundations with segmented VPCs or VNets, private service endpoints, explicit egress controls, and connectivity to on-premises if required.
- Centralised logging, metrics, and traces with immutable storage and retention aligned to policy.
- Policy as code, enforcement and drift detection, and pre-approved configuration baselines for common services.
- Secure workload blueprints for containers, serverless, and data platforms, tied to image signing and vulnerability management.
Build the landing zone with Infrastructure as Code, then integrate it into CI pipelines so every change is reviewed and auditable. If Kubernetes is part of your platform, include cluster bootstrapping, policy packs, and GitOps controllers from day one. Our hands-on guide to provisioning EKS in minutes shows how to keep clusters fully declarative with Terraform. See the Terraform EKS module walkthrough.
Evidence and continuous compliance by design
Audits should be a by-product of daily operations, not a crisis event. Bake evidence generation into pipelines and platforms.
- Change management: every infrastructure and application change goes through pull requests, automated checks, and approvals. The repository history becomes your audit trail.
- Policy enforcement: use policy as code to block non-compliant infrastructure before it is provisioned. Continuously scan live environments for drift and remediate automatically.
- Tamper-evident logs: enable object-level immutability and legal hold features for audit and security logs. Protect time synchronisation and chain of custody.
- Incident readiness: ensure alert routing, on-call coverage, and runbooks are tested. Record exercises and outcomes as evidence.
If you are preparing for a cloud migration or a major refactor, our primer on cloud migration tools outlines how to assess, execute, and validate with less downtime and better traceability.
Commercial and procurement considerations
Security features are necessary but not sufficient. Commercial constraints and contract language can create hidden compliance risk.
- Support and SLAs: define response times and escalation paths that match regulatory tolerance for outages or incidents.
- Data processing and deletion: ensure clear data processing agreements, subprocessor visibility, and verifiable data deletion procedures at contract end.
- Exit strategy: keep workloads portable using open standards and IaC. Avoid one-way dependencies that lock you into non-negotiable terms or regions.
- Cost controls: regulated does not have to mean expensive. Right-size, use autoscaling and reservations where appropriate, and review storage classes and telemetry retention. Measure and iterate to avoid creep.
Common anti-patterns to avoid
- Treating the cloud provider certification list as your compliance programme. Certifications help, but they do not replace your own controls and evidence.
- Relying on perimeter security while leaving identities over-privileged and logs mutable.
- Allowing manual production changes that bypass code review and policy checks.
- Mixing regulated and non-regulated data in the same environment without clear boundaries and monitoring.
A 90-day path to a compliant baseline
- Confirm regulatory scope and risk appetite. Finalise data classification and residency rules.
- Choose target regions and draft the landing zone reference architecture.
- Implement identity baseline, MFA, SSO, and role design. Lock down break-glass access.
- Build networking baselines with private endpoints and egress controls. Connect to on-premises if needed.
- Stand up central logging, metrics, and traces with immutable retention. Integrate with your SIEM.
- Introduce policy as code and IaC pipelines, then enforce controls on one pilot workload.
- Harden Kubernetes or compute baselines, introduce image signing and vulnerability gating.
- Run game days for incident response and restore tests. Record evidence and close gaps.
How Tasrie IT Services can help
Tasrie IT Services specialises in DevOps, cloud native platforms, Kubernetes, and automation for regulated environments. We partner with engineering, security, and compliance teams to deliver measurable outcomes, for example faster release cycles with policy guardrails, lower incident risk with better observability, and lower spend through right-sizing and automation.
- DevOps consulting and CI/CD automation with policy and evidence baked in
- Cloud native and Kubernetes platform engineering with GitOps and compliance guardrails
- Infrastructure as Code and landing zone implementation
- Monitoring and observability, incident response readiness, and cost optimisation
If you are evaluating cloud solutions for a regulated workload, we can help you define the control objectives, design a compliant landing zone, and migrate with confidence. Start a conversation at Tasrie IT Services.
Further reading and references
- UK NCSC, Cloud Security Principles: NCSC Cloud Security Principles
- UK Information Commissioner’s Office, UK GDPR overview: ICO UK GDPR guide
- PCI Security Standards Council, PCI DSS: PCI DSS
- US HHS, HIPAA Security Rule: HIPAA Security Rule
- Cloud Security Alliance, Cloud Controls Matrix: Cloud Controls Matrix
- CIS Kubernetes Benchmark: CIS Kubernetes Benchmark
- NIST SP 800-207, Zero Trust Architecture: NIST SP 800-207 Zero Trust Architecture